REVEN 2.3: 32-bit symbols, Current Process Information, and more
Tetrane is happy to announce the recent release of REVEN 2.3.
REVEN is an automated Reverse Engineering Platform designed to go x10 faster & x10 deeper using Timeless Analysis. Technically, REVEN captures a time slice of a full system execution (CPU, Memory, Hardware events) to provide unique analysis features that speed up and scale your reverse engineering process.
This article covers the most important changes introduced in the REVEN 2.3 release.
In details, this release features support for 32-bit symbols in x86 and x64 traces, current process API and new GUI improvements.
I’ll take the 32-bit symbols, please
While REVEN, working at the CPU level, can display the execution trace of a software scenario independently from the OS under analysis, higher-level information such as the current process or executed symbol is specific to the OS of the scenario.
Such information is central to the reverse engineering process. In REVEN, we call it OSSI, for OS Specific Information. OSSI helps reverse engineers to find their marks easily in the execution trace and the associated states available in REVEN such as the Backtrace.
As such, allowing to access symbol information for 32-bit executables started in 64-bit Windows, and 32-bit executables started in 32-bit Windows, was one of the most requested REVEN feature.
This is why we are pleased to report that, starting with REVEN 2.3, OSSI is fully supported for the analysis of scenarios with the following Windows configurations:
| Configuration/OS | Windows 7 | Windows 10 |
|---|---|---|
| 64-bit executable, 64-bit OS | Supported | Supported |
| 32-bit executable, 64-bit OS | Supported | Supported |
| 32-bit executable, 32-bit OS | Supported | Supported |
You can try REVEN on a 32-bit Windows scenario by testing online our demo of a formbook analysis, a well known stealer malware.
And the current process is…
Recently, we published a blog article about system calls, and finding out which process were responsible for making them. This tutorial resulted in a python script using our API to implement a heuristic way of recovering the process responsible for a system call using the backtrace. The core of that logic looked like the following:
for ctx in search.symbol(symbol): # for each call to our syscall symbol
# find appropriate stack depending on heuristic
if is_user_stub:
stack = ctx.stack
else:
stack = ctx.stack.prev_stack()
# look in the frames of the call stack to find a ring 3 binary
for frame in stack.frames():
fr_ctx = frame.first_context
ring = fr_ctx.read(reven2.arch.x64.cs) & 3
if ring == 0:
continue
location = fr_ctx.ossi.location()
if location is None:
continue
binary = location.binary
if binary.filename.endswith(".exe"):
# Return our context id and the binary name
yield (ctx, binary)
REVEN 2.3 adds a new process() method to the OSSIContext object, allowing to retrieve the currently active process
at any point of the trace. Let’s use it to get the process responsible for making our system call…
for ctx in search.symbol(symbol): # for each call to our syscall symbol
# Return our context id and the binary name
yield (ctx, ctx.ossi.process().name)
Much shorter, and also more correct, as it is no longer a heuristic method!
For completeness, we pushed a new version of the script on our github.
In this new version, astute readers may notice that we updated the way you can connect to a REVEN scenario: previously,
it was necessary to specify the port to the REVEN server, that would change between each subsequent openings of the
scenario. Now, you only need the address of the REVEN project manager (defaults to http://localhost:8880 and won’t
change in a typical installation) and the scenario name.
This allows us to start the script with:
$ python syscallstack_2.3.py bksod "^NtCreateFile$" # Project name "bksod" won't change in future openings of scenario
Rather than:
$ python syscallstack.py --port 39221 "^NtCreateFile$" # Project port "39221" will change next time we open the scenario
GUI ergonomic improvements
REVEN 2.3 brings several improvements to the GUI: the status bar provides vital information about the current position in the trace at any time, while the new menu makes it easier to access the various features of the GUI. Lastly, the guided tour attempts to smoothen the learning curve a bit for new users.
Status bar
Browsing traces that are several billion instructions long can prove a significant challenge. The first step to ease navigation is to be aware of one’s current location. The new status bar we added at the bottom of the Trace view serves the purpose of the “you are here” sign you can find on maps.
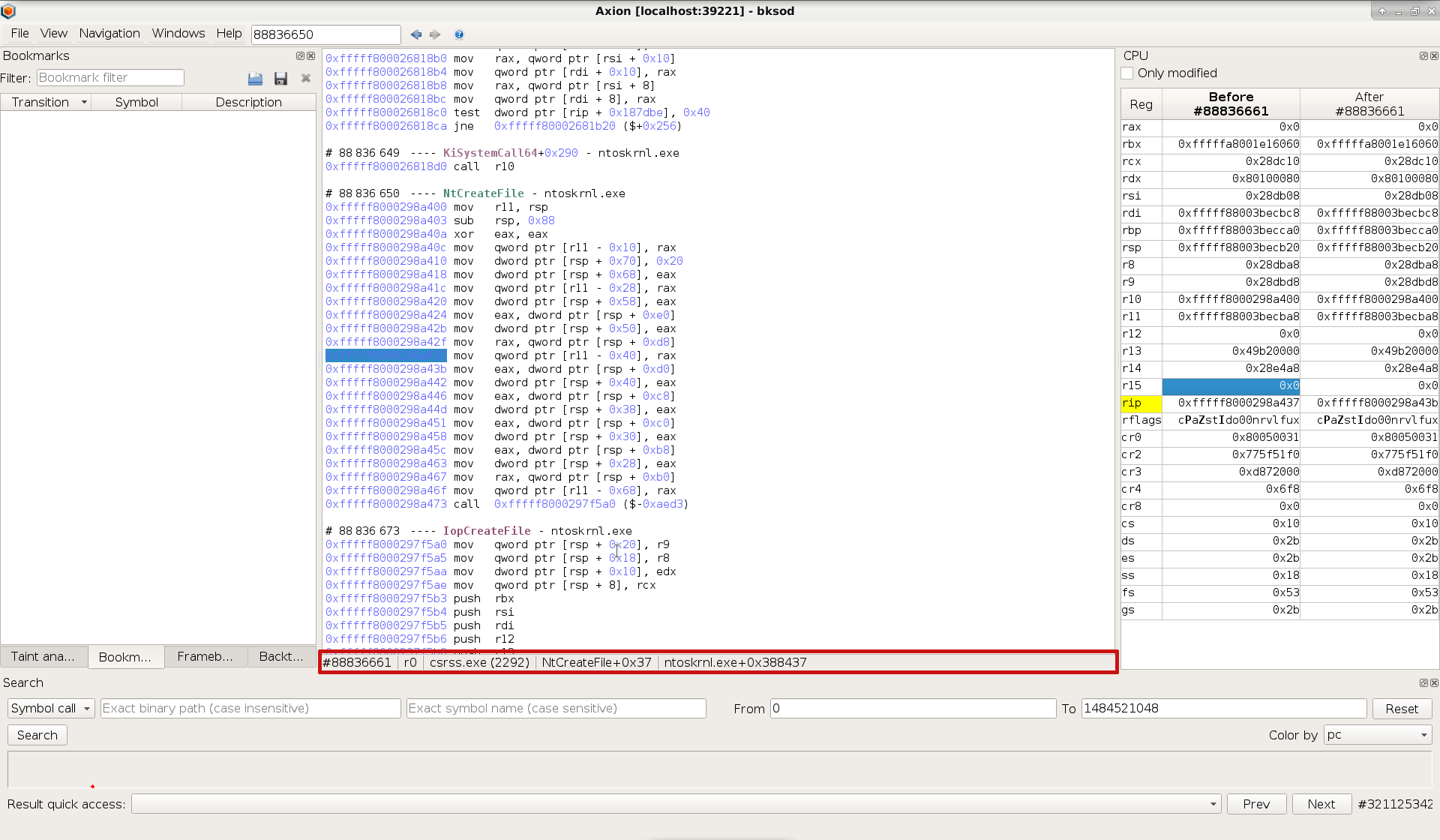
It provides information about the current transition, ring, process, symbol and binary. This information is updated each time you move in the trace. Moreover, you can right-click the bit of information to quickly copy it to clipboard.
New Menu
Here’s a picture of the GUI’s new menu:
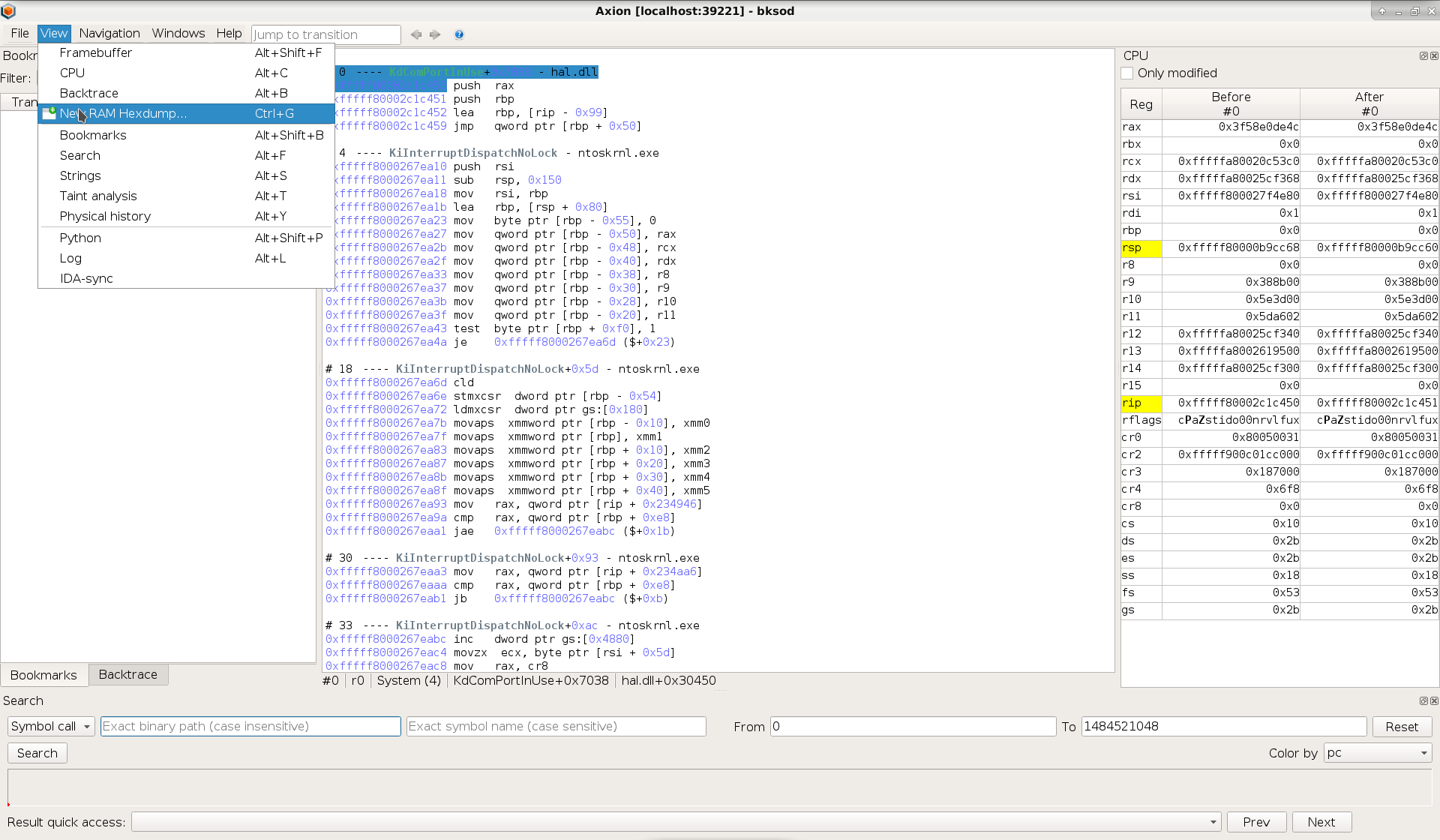
The biggest change is on the “View” menu, that was reorganized so as to adopt a flat structure, making the various features more readily available.
Guided Tour
The guided tour has been added for new users to get familiar with the GUI. It is a tutorial wizard that walks the user through each feature and widget of the GUI.
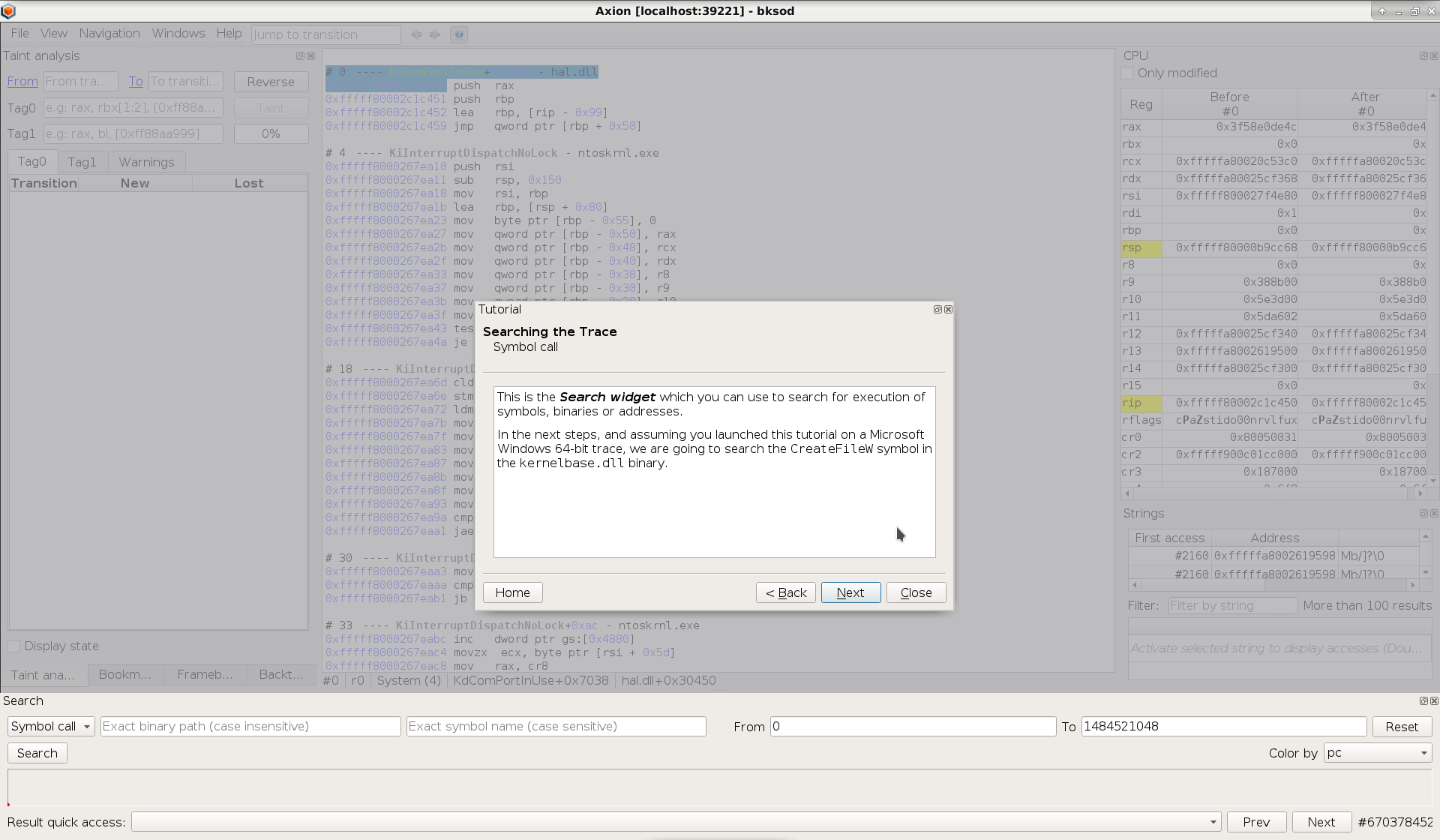
The guided tour is also available in REVEN’s demos, along with more specific tutorials for some of them, such as the VLC media player exploit demo.
Other improvements
Other improvements include:
- the addition of markers for outdated scenario resources directly in the
Scenario Listtab of the Project Manager, that makes it easier to detect scenarios that should be replayed after an upgrade, - improved stability for the autorecord feature, and
- improved performance of the backtrace widget.
The full list of improvements and fixes is available in the release notes included with all REVEN distributions.
Want to try REVEN 2.3? It is now live in our online demos, so just pick one from our demo catalog!

