Tetrane's BLOG
Our blog is moving to eShard

Following the acquisition of Tetrane by eShard, new articles will be published on the eShard blog starting today. This post will only provide links to the newly published articles (you can still find all the pre-existing content on the blog home): Retrieve the drive letter from a device name on...
Announcing Tetrane acquisition by eShard

I am really excited to announce that eShard has acquired Tetrane. At Tetrane, we have spent years rethinking and reinventing how timeless analytics can contribute to vulnerability research. It’s been a crazy, exciting, and fun journey, during which we’ve built an incredible team of very talented people. This is the...
Fine-tuned Windows scenarios: debugger-assisted recording with WinDbg
In this article we present a new way to leverage WinDbg to interactively control the VM during the recording of a scenario: this enables the user to more intuitively get to the point of interest and check conditions to control the execution, resulting in a more precise recording. You can...
Announcing REVEN version 2.11

Tetrane is pleased to announce the release of REVEN Enterprise, REVEN Professional and REVEN Free 2.11. REVEN is a Timeless Debugging and Analysis (TDnA) Platform designed to go x10 faster & x10 deeper while reverse engineering. Technically, REVEN captures a time slice of a full system execution (CPU, Memory, Hardware...
Keep timeless analysis records to the point with REVEN and GDB

How to get the shortest record for a scenario? Given that a short record is synonymous with less recorded, replayed and analyzed instructions, this is a frequent question we receive about REVEN usage, with the goal of speeding up scenario replay and facilitating subsequent analyses with the Axion GUI and...
A tour of the Rust and C++ interoperability ecosystem

Rust is a programming language with a very interesting value proposition when coming from C++, and so it is only natural to see increasing usage of it in REVEN’s codebase. We have some internal tooling using the language, the frontend for our Windbg integration is written in Rust, and REVEN...
Automatic post-fuzzing triage and automation using REVEN
08 Mar 2022
by
Louis
,Quentin
and Mickaël
-
Technical
-
Reverse Engineering
REVEN
Fuzzing
AFL
Workflow API
As those of you lucky enough to attend the great OffensiveCon 2022 might be aware, we are developing a Fuzzing & Triage platform based off REVEN Enterprise Edition. The platform aims at automating root cause analysis by deriving advanced information about crashes found by a fuzzer, such as the origin...
Yes, race conditions can be detected with a single core Timeless Debugging and Analysis platform!
01 Mar 2022
by
Louis
and Quentin
-
Technical
-
Reverse Engineering
REVEN
Buffer overflow
Taint
Race Condition
Vulnerability Detection
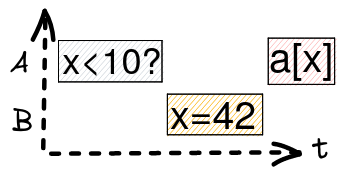
As REVEN emulates a single core machine, a frequent question we receive is if it is possible to use REVEN to analyze race conditions. There can be a lot of confusion around what is possible or not, so in this article we hope to address this by giving examples of...
REVEN Free Edition - Available as a VM

We are happy to announce that REVEN Free Edition is now also available as a VM for an easy installation (QEMU, Hyper-V, VMWare). Below are the details to follow. Download Download REVEN Free Edition download page. How to configure the VM The REVEN in a VM installation provides you with...
REVEN Free Edition - Install Party

Join us for the REVEN Free Edition Install Party on December 21 at 10am EST -> If you are curious about REVEN, its capabilities, and did not yet took time to discover it, it is the perfect occasion for you to install REVEN Free Edition and try it out. You...
Older Posts
