Announcing REVEN version 2.7
Tetrane is pleased to announce the release of REVEN Enterprise and REVEN Professional 2.7.
REVEN is an automated Reverse Engineering Platform designed to go x10 faster & x10 deeper using Timeless Analysis. Technically, REVEN captures a time slice of a full system execution (CPU, Memory, Hardware events) to provide unique analysis features that speed up and scale your reverse engineering process.
REVEN is a very precise platform that lets you see what happens in the execution trace of a system, at the level of the individual instruction. While accuracy offers a solid foundation for analysis, sometimes you want to see synthetic information about the binary or the scenario you have recorded.
In REVEN version 2.7, we strived to provide you with a “bird’s eye view” over the execution trace. This translates to new features and tools designed to help you extract the important information about what happens in your scenarios at a glance.
This article covers these new features and tools and the other important changes introduced in the REVEN 2.7 release.
Filtering the trace
REVEN works system-wide for the sake of exhaustivity. It allows nice unique features such as backward and forward data flow tainting, but sometimes what you really want to see is your user-space process.
Axion, REVEN’s GUI, now proposes a long-awaited Filter widget, that allows you to see at a glance which processes are present in a trace, and specify which ones are of interest to you.
You can even filter by ring, so that you can see only user space instructions if you’re not interested in what happens in the kernel!
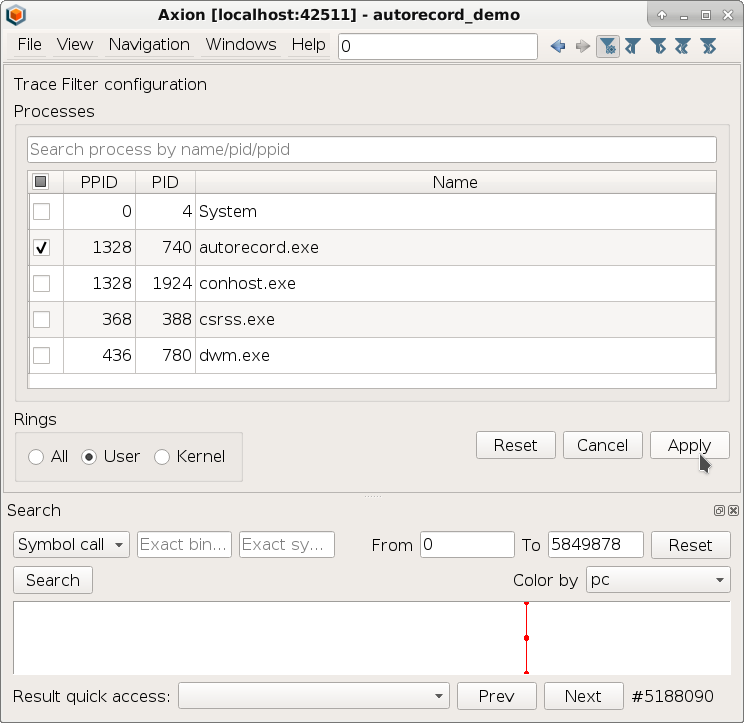
The Trace view then reflects which ranges of instructions belong to the specified filter, and allows to browse between these ranges, skipping the filtered out transitions. In the following video, we use the Filter widget to filter first on user space instructions, and then only on the autorecord.exe process, and lastly we browse the filtered trace:
Filtering the trace has been a long-planned feature internally, so the team is very glad to finally have its first iteration out of the door 🎉!
Use-After-Free vulnerability detection
Use-After-Free (UAF) is an important class of exploitable vulnerabilities whose prevalence increased a lot in recent years1.
REVEN version 2.7 includes a notebook that allows you to search for UAF vulnerabilities in traces produced by REVEN!
We used the script to automatically detect UAF in both user and system scenarios that we had previously analyzed manually in this blog.
The script is also available on our GitHub. It leverages REVEN’s taint API to detect potential UAFs, which is something that we might write about more in details someday.
You can read this blog article which is dedicated to this feature.
Here’s a small look at the script in action on BlueKeep. Users just need to fill out a cell of parameters, and then let the script do its magic!
Reports
We believe REVEN must bring you as much information as possible out of trace so that Points of Interest are there ready for you to use. With that goal in mind, REVEN 2.7 comes with new reports that you can use and tailor to your needs.
File activity report
Did this piece of malware create any files? What existing files did it read from or write to?
We are releasing on GitHub a tool that reports file operations, such as creation, deletion and read/write accesses.
The following video demonstrates the use of the script on a scenario where a file is written to in notepad.exe.
It is easy to find the write file events from the output of the script.
Crash quick report
So, did my process crash? Did my PoC trigger the vulnerability and cause the dreaded Blue Screen of Death?
With REVEN 2.7, you can now answer these questions by executing a simple Python script. This tool detects and reports system crashes and user exceptions that occur in a REVEN scenario.
We ran the script on various toy scenarios and real CVE PoCs and exploits, find below some sample outputs.
We are releasing the script on GitHub
ud2_amd64
| Mode | Process | Context | BugCheck | Cause | Exception transition |
|---|---|---|---|---|---|
| User | ud2_amd64.exe (1304) | Context before #27884183 | N/A | illegal instruction (0x10000002) | #27880023 invalid opcode while executing ud2 |
div_by_zero_amd64_0
| Mode | Process | Context | BugCheck | Cause | Exception transition |
|---|---|---|---|---|---|
| User | div_by_zero_amd64.exe (856) | Context before #13062259 | N/A | integer division by zero (0x10000003) | #13058082 divide error while executing div eax |
CVE-2019-1347_peparsercrash_minimal
| Mode | Process | Context | BugCheck | Cause | Exception transition |
|---|---|---|---|---|---|
| System | explorer.exe (1408) | Context before #77895973 | 0x50 | page fault while reading address 0xfffff8035b2ae7ff | #77895280 page fault while executing mov rax, qword ptr [rcx + rdx] |
bksod (BlueKeep, aka CVE-2019-0708)
| Mode | Process | Context | BugCheck | Cause | Exception transition |
|---|---|---|---|---|---|
| System | svchost.exe (1004) | Context before #1231562417 | 0x3b | access violation (0xc0000005) | #1231550326 page fault while executing mov r12d, dword ptr [rsi + 8] |
CVE-2020-16898
| Mode | Process | Context | BugCheck | Cause | Exception transition |
|---|---|---|---|---|---|
| System | System (4) | Context before #2423351 | 0x139 | stack buffer overrun (0xc0000409) | #2423247 interrupt 41 while executing int 0x29 |
More automatic recording
In REVEN 2.6, we added automatic recording of binaries from the Project Manager.
For version 2.7, the more powerful ASM stub automatic recording is now available as well (Enterprise Edition). ASM stub recording grants you the ability to automatically start recording when a specific instruction is executed within the guest, and then stop it when a specific instruction is executed.
Concretely, this means that the following program:
#include <stdio.h>
#include "asm_stubs.h"
int main() {
int i = 0;
for (; i < 5; ++i) {
printf("i=%i\n", i);
}
printf("Printed before record\n");
host_start_record();
for (; i < 20; ++i) {
printf("i=%i\n", i);
}
host_stop_record();
host_commit_record();
printf("After record!\n");
return 0;
}
will start recording right after printing Printed before record\n, and stop right before printing After record!\n.
The asm_stubs.h header can be found as part of the “ASM stub utility (C/C++ header)” in the Downloads page of the
Project Manager.
Improved Linux OSSI support
While REVEN, working at the CPU level, can display the execution trace of a software scenario independently from the OS under analysis, higher-level information such as the current process or symbol is specific to the OS.
Such information is central to the reverse engineering process. In REVEN, we call it OSSI, for OS Specific Information. OSSI helps reverse engineers to find their marks easily in the execution trace and the associated states available in REVEN such as the Backtrace.
REVEN supports Windows 7 and Windows 10 OSSI out of the box, but up until now, supporting Linux VMs was less integrated and required user intervention.
Starting with REVEN 2.7, the Linux OSSI works out-of-the-box for the supported Debian and Fedora versions, you just need to record and replay your scenario as you would do with a Windows scenario, and then the new kernel symbols are available to you in the GUI:
And More
- The ability to record QEMU VMs with more than 3GB of RAM.
- A much more efficient VM preparation process, shortening the time before you can record a VM.
- While working with WinDbg on a REVEN trace, Axion can now be synchronized with WinDbg, so that whenever WinDbg requests a new transition with a debugging command, the same transition is selected in Axion.
- API and correctness fixes to the taint.
The full list of improvements and fixes is available in the release notes.
Want to try REVEN? An extensive set of learning scenarios is available online, so just pick one from our demo catalog! Tutorials are available in most demos.
Interested in REVEN? Compare the features of REVEN Professional and REVEN Enterprise.
-
Juan Caballero, Gustavo Grieco, Mark Marron, and Antonio Nappa. 2012. Undangle: early detection of dangling pointers in use-after-free and double-free vulnerabilities. In Proceedings of the 2012 International Symposium on Software Testing and Analysis (ISSTA 2012). Association for Computing Machinery, New York, NY, USA, 133–143. DOI:https://doi.org/10.1145/2338965.2336769 ↩

