Tetrane's BLOG
Announcing REVEN version 2.5

Tetrane is happy to announce the release of REVEN 2.5 Enterprise and Professional. REVEN is an automated Reverse Engineering Platform designed to go x10 faster & x10 deeper using Timeless Analysis. Technically, REVEN captures a time slice of a full system execution (CPU, Memory, Hardware events) to provide unique analysis...
Automated analysis of crashes or malware, and integration with fuzzers
06 May 2020
by
Mathieu
-
Tutorial
Automation
-
Demo
Automation
Workflow API
Analysis API
Scenario recording

Analyzing a crash within a fuzzing process or not, capturing and analyzing malware activities, those tasks can now be fully automated with REVEN. It’s also easy to plug it into your tool chain or customize it. This demo presents the entire automated workflow: starting a VM. loading and launching the...
REVEN DEMO - Comparing the dynamic execution on 2 systems (3/3)

This video continues the analysis of CVE-2019-1347. It demonstrates how to compare 2 executions, on a vulnerable system vs non-vulnerable system to extract valuable information about the vulnerability. The first video demonstrated how to move quickly from a system crash to the input file responsible and the WinDbg Integration. The...
REVEN DEMO - Taint and IDA Integration (2/3)

This video continues the analysis of CVE-2019-1347. This part of the demo uses data flow tainting forward. It also shows the IDA integration to get both the static & the dynamic view of the application under analysis. The first video demonstrated how to move quickly from a system crash to...
REVEN DEMO - From a crash to the input file and WinDbg Integration (1/3)

In this video, we show how to quickly move from a system crash to the input file at its origin. It demonstrates the usage of REVEN features like the data flow tainting and the integration with WinDbg. This demo is related to the CVE-2019-1347 (“When a mouse over a file...
REVEN Tainting and APIs for automation

This demo focuses on 2 areas: The REVEN data flow tainting feature that makes it easy to follow data across processes using IPC or local network communications The REVEN Python API to automate analysis tasks, used here for data tainting. The example is based on the application Tokio chat with...
Recording a Crash with REVEN Project Manager

In this video, we will have a look at the Project Manager UI, which is the tool REVEN provides to enable users to manage virtual machines and scenarios. As far as scenarios are concerned, the Project Manager allows to record scenarios and generate data resources for the RE analysis. We...
Analyzing CVE-2018-8653 with REVEN: Use-after-Free in Internet Explorer Scripting Engine
10 Mar 2020
by
Luc
-
Technical
-
Use After Free
UaF
Reverse Engineering
Garbage Collector
Memory Management
CVE
Demo
REVEN
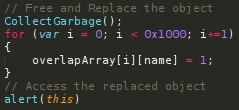
In this post we will have a look at the proof of concept for CVE-2018-8653 that comes from a very interesting blog post from Philippe Laulheret et al. at MacAfee Labs. To summarize, the vulnerability exploits various seemingly innocent behaviors in Internet Explorer’s scripting engine (jscript.dll) to trigger a use-after-free...
Tetrane launches REVEN Professional Edition

Tetrane launches REVEN Professional Edition! You were many to request and wait for a lighter, more accessible, more affordable version of REVEN. Here it is! REVEN Professional Edition democratizes full-system timeless analysis for vulnerability and malware analysis. Now, it is directly available for purchase on TETRANE website REVEN Professional Edition...
Analysis of CVE-2019-0708, a.k.a. BlueKeep, with REVEN: Another point of view
22 Jan 2020
by
Luc
-
Technical
-
Use After Free
UaF
Reverse Engineering
Garbage Collector
Memory Management
CVE
Demo
REVEN

Bluekeep (CVE-2019-0708) is a security vulnerability that was discovered in Microsoft’s Remote Desktop Protocol, which allows remote code execution. At least one analysis already describes precisely this vulnerability with a specific approach. This blog post aims to demonstrate how REVEN can be used to analyze the crash, the root cause...
Newer Posts Older Posts

