Tetrane's BLOG
Analyzing an Out-of-Bounds read in a TTF font file

In this post we will analyze some specific points from the proof of concept for CVE-2019-1244, that has been found by Mateusz @j00ru Jurczyk. This vulnerability is a user-mode out-of-bounds read in Microsoft DirectWrite function dwrite.dll!sfac_GetSbitBitmap while processing a TTF font file. Our starting point is a first recording of...
REVEN 2.3: 32-bit symbols, Current Process Information, and more

Tetrane is happy to announce the recent release of REVEN 2.3. REVEN is an automated Reverse Engineering Platform designed to go x10 faster & x10 deeper using Timeless Analysis. Technically, REVEN captures a time slice of a full system execution (CPU, Memory, Hardware events) to provide unique analysis features that...
Who's calling? Finding out which process made a system call

The version 2.2 of REVEN saw the addition of the Analysis Python API, that lets you automate the analysis of a scenario using scripts. The API sparkled the interest of our users and gave them inspiration to handle many use cases by scripting. One of these use cases is going...
CVE-2019-1347: When a mouse over a file is enough to crash your system
CVE-2019-1347 is a vulnerability disclosed in october 2019 by Mateusz @j00ru Jurczyk in the Windows relocation mechanism when parsing a PE file. By simply placing your mouse cursor over the Proof of Concept file, a Blue Screen Of Death is triggered. We thought the original description could be positively completed...
REVEN 2.2: Python API, Automatic Recording, and more

Tetrane is happy to announce the recent release of REVEN 2.2. REVEN is an automated Reverse Engineering Platform designed to go x10 faster & x10 deeper using Timeless Analysis. Technically, REVEN captures a time slice of a full system execution (CPU, Memory, Hardware events) to provide unique analysis features that...
Analysis of the Uroburos malware with REVEN
12 Jun 2019
by
Luc
and Mathieu
-
Technical
-
Reverse Engineering
Malware Analysis
Windows Kernel
Demo
REVEN

In this post, we present how Timeless Analysis can be used to analyze a few mechanisms of a Uroburos recent version. We use REVEN and its integration with Volatility and IDA to detect indicators of compromise, analyze the dropping mechanisms and circumvent tricks the malware uses to hide itself. The...
Windows boot from UEFI to kernel
20 May 2019
by
Mathieu
-
Technical
-
Reverse Engineering
Windows Kernel
Windows boot
UEFI
Demo
REVEN

Getting full visibility into the Windows 10 OS’ boot mechanisms is challenging. REVEN opens up a new world of possibilities with its timeless analysis technology! We used REVEN to record the Windows OS’ boot process, all the way from before the UEFI firmware transfers control to the boot process, to...
Full visibility of a Windows Kernel Bug with Timeless Analysis (CVE-2018-8410)
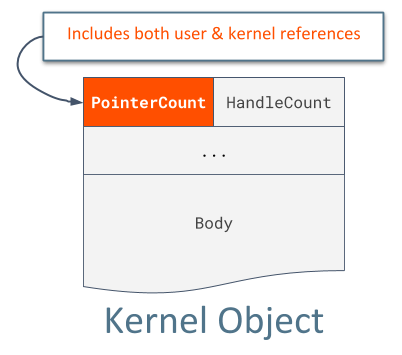
One of the situations where REVEN (aka Tetrane) really shines is digging into undocumented kernel mechanisms, especially in cases where WinDBG abstracts information away from the user. In the following video, we will analyze a reference counting bug in the Windows Kernel (CVE-2018-8410 published by Google Project Zero) and try...
Updated Analysis of PatchGuard on Microsoft Windows 10 RS4
Since Windows 64b, PatchGuard has been of great interest in Windows security. In this white-paper, you will access our research done using REVEN v2. For most iterations of its development, several people have analyzed its main mechanisms and internals which, many times, led to a functional bypass. Researchers seem to...
Analysis of VLC Exploit Arbitrary Code Execution (CVE-2018-11529)
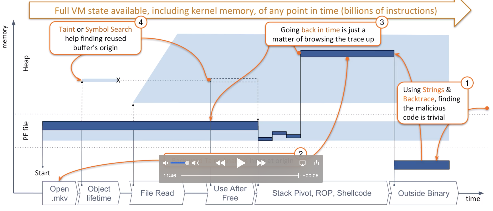
This is the analysis of VLC Exploit Arbitrary Code Execution (CVE-2018-11529) done REVEN v2. It leverages our timeless analysis technology and several key features:
Data Tainting
Memory History
Backtrace
etc.
Newer Posts Older Posts

